Use ssh-copy-id on Server 1, assuming you have the key pair (generated with ssh-keygen ): ssh-copy-id -i /.ssh/idrsa user@server2hostname. Now you should be able to ssh into Server 2 with ssh using the private key. Ssh -i /.ssh/idrsa user@server2hostname. Use of proper SSH key management tools tools is recommended to ensure proper access provisioning and termination processes, regularly changing keys, and regulatory compliance. SSH keys can be generated with tools such as ssh-keygen and PuTTYgen. These tools ask for a phrase to encrypt the generated key with. PGP / GPG Private Key Protection.

This post is older than a year. Consider some information might not be accurate anymore.
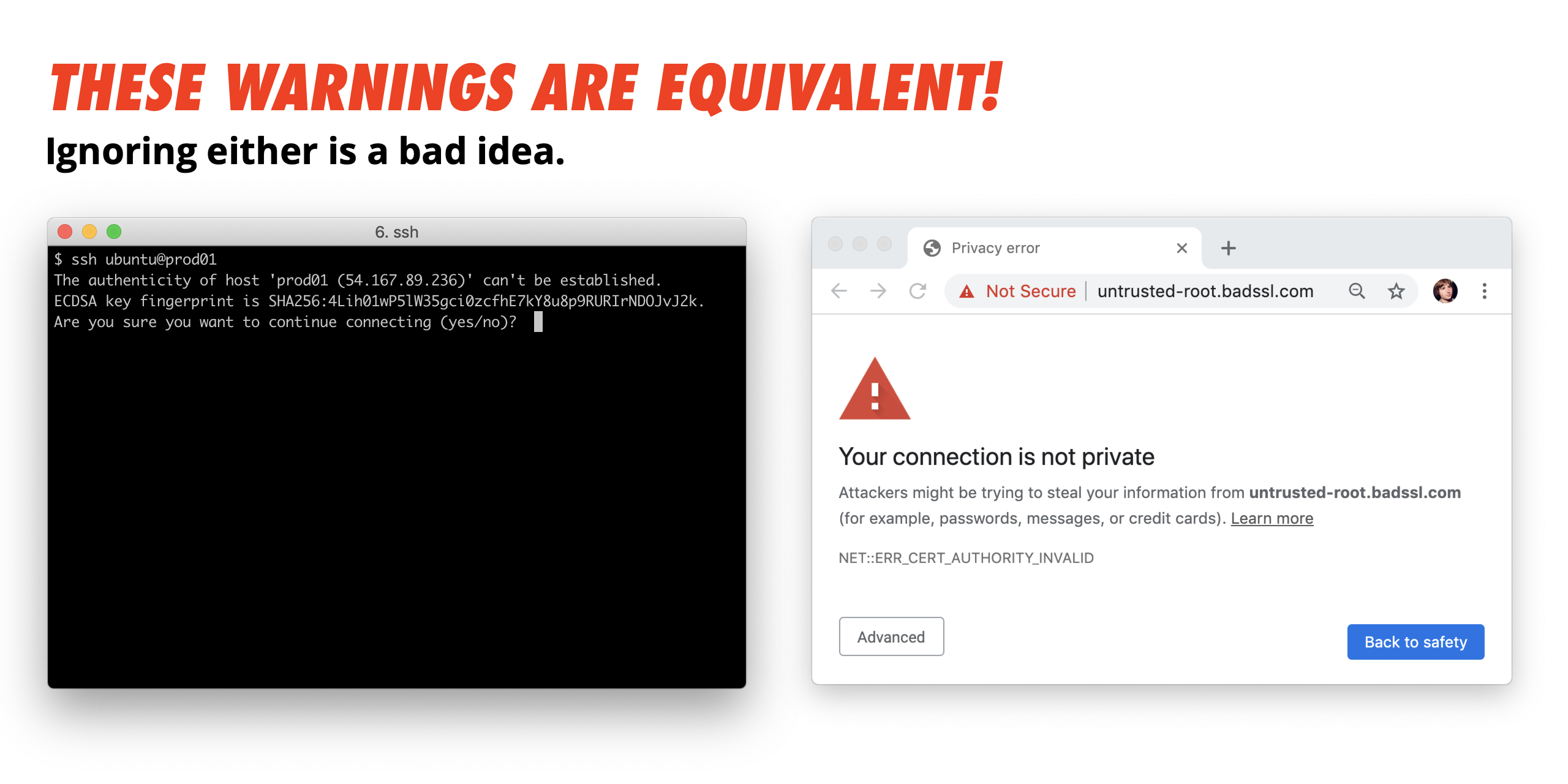
Question: When Generating And Storing SSH Private Key Pairs, The Following Permissions Mask Is Required. Using This Mask Prevents Unauthorized Access And Is Enforced By The Ssh Agent When Loading Keys. 600 666 000 011 If Key Based Authentication Has Been Enabled Within The SSH Server Configuration, Local Users May Place Keys In This File To Authorize Those Keys. Sep 18, 2019 It will then use this key to establish a secure SSH connection with the worker nodes, without saving the private key on any master node storage. You can review the copyfile.py on the master node or on GitHub. In the getprivatekey function, you can read the secret value, which includes the private key. Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the /.ssh directory. You can specify a different location, and an optional password (passphrase) to access the private key file. If an SSH key pair with the same name exists in the given location, those files are overwritten.
MobaXterm is also a more convenient ssh client like putty. Session management in the professional version is very handy. Since MobaXterm comes with cygwin, ssh is also available in the local terminal. To eliminate the hassle for entering the password (especially if security compliance requires you to change the password every month), ssh keys are a more secure and convenient method for authentication on servers. This post illustrates how you do it with MobaXterm.
Before using ssh, MobaXterm requires a persistent home directory. Go to Settings and set the persistent home directory.
First step is to generate the ssh key, therefore open a local terminal and generate a key (rsa) with this command:
The output
The second step is to export the public key to the servers, with respective logins, to the authorized keys file. Replace user@host to your needs.
You may need to create the ssh folder first in your home directory on the remote machine.
Git Use Private Ssh Key
or combine it within the ssh command
Public Key
Edit: After some instruction with my co-worker, you have to change the session to use the ssh-key (see picture below).